Intro to Networking - Virtual Private Networks & Tunneling
Overview
This introductory article explains what Virtual Private Networks (VPNs) are used for, the two main categories of VPNs, as well as how tunneling works.
Table of Contents
What are VPNs?
Virtual Private Networks, or, VPNs, provide a way for Hosts to communicate within a Local Area Network from outside the Physical LAN boundaries; which practically includes, the Internet.
VPNs are generally categorized by either of two types:
- Remote Access
- Site-to-Site
In a Remote-Access VPN Scenario, a VPN Client, such as a Laptop or Smartphone, establishes a remote connection to a VPN Server, such as a Router, in order for the Client to communicate on the LAN from say, across the Internet.
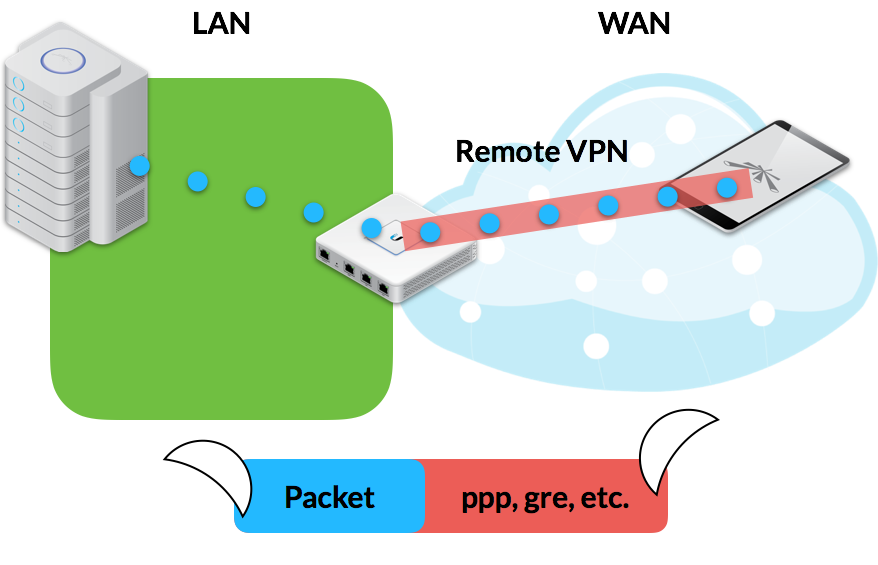
Image 1: Remove-Access VPN
Under a Site-to-Site VPN Scenario, two or more VPN Routers create end-to-end connections in order to allow LAN traffic to traverse the WAN.
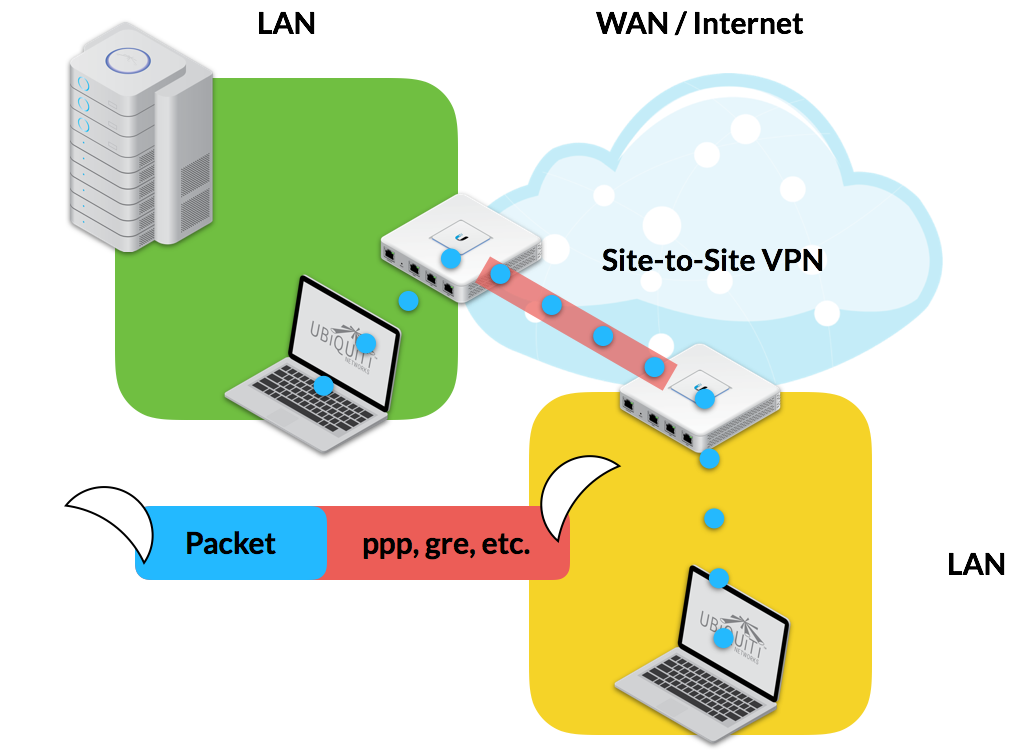
Image 2: Site-to-Site VPN
What is Tunneling?
In both scenarios, VPN Traffic reaches the intended Network Endpoint through a process called Tunneling.
Tunneling surrounds the original IP Packet with an extra layer of encapsulation, called the Carrier Protocol, to help the data successfully traverse the WAN inconspicuously with the help of encryption protocols.
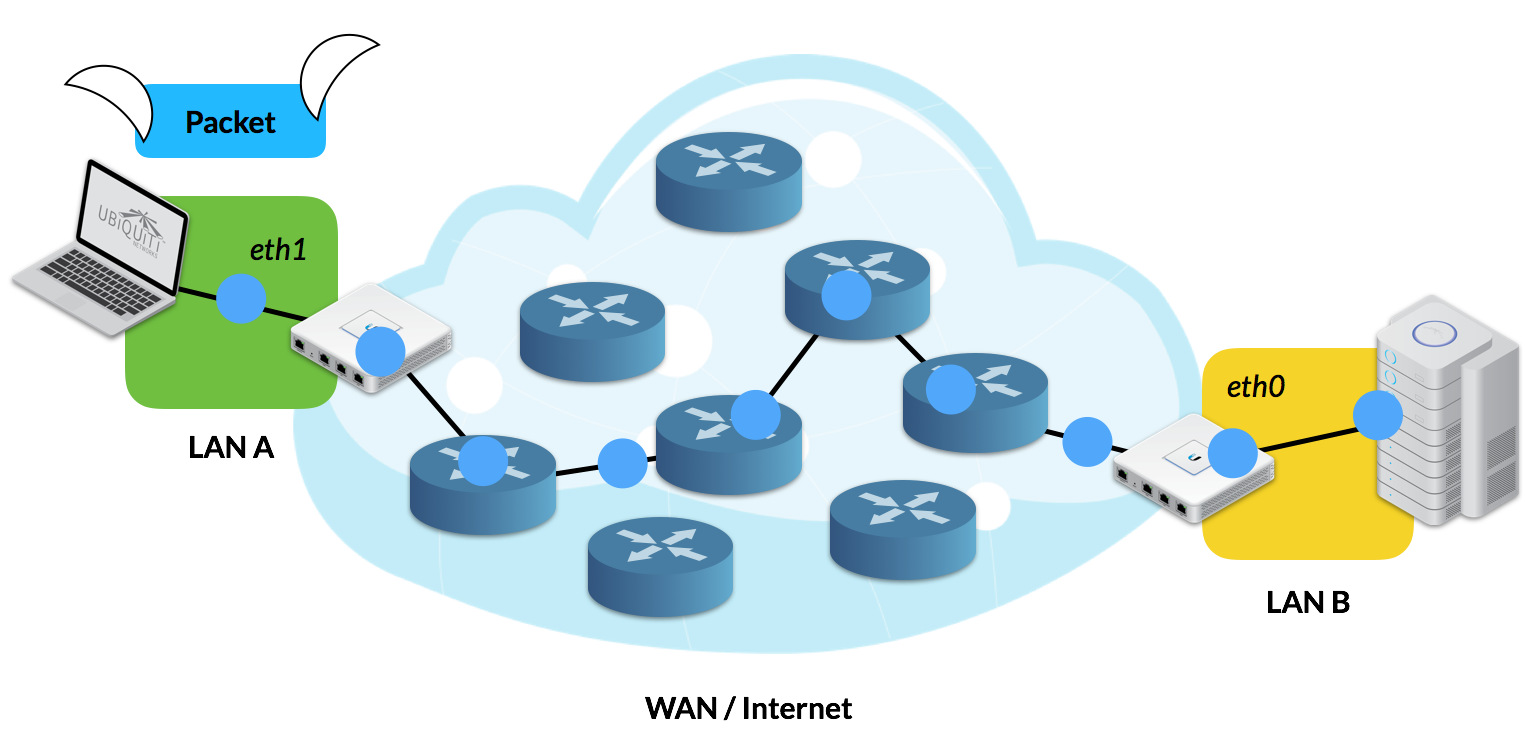
Image 3: Normal IP packet routing from end-to-end without tunneling.
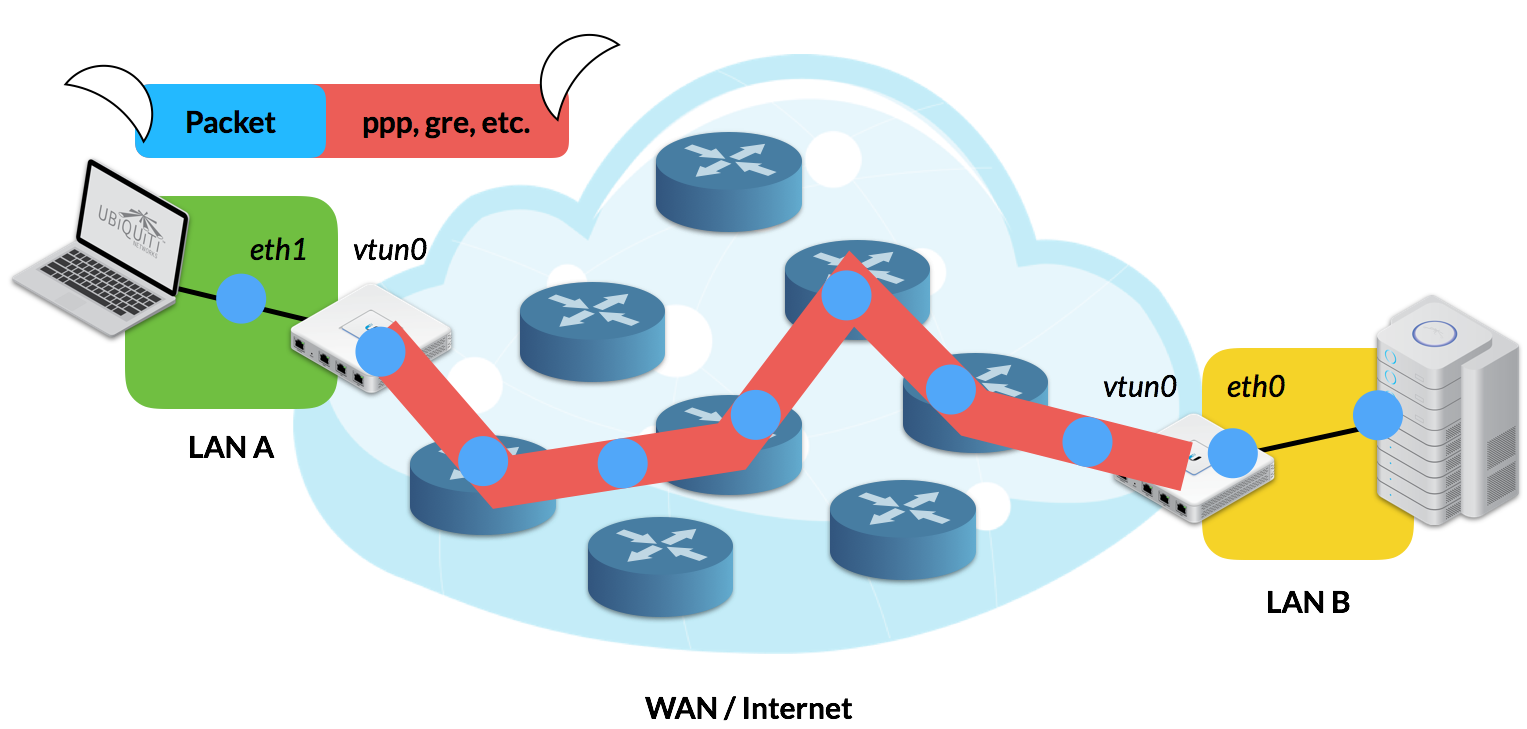
Image 4: Site-to-Site VPN illustrates tunneling from end-to-end.
Tunneling Analogy
Take a look at the analogy below. Tunneling is analogous to a Moving Company that helps load and unload Boxed Furniture to the new Home.
- The Furniture is the Application-Layer Data.
- The Box is the IP Packet.
- The Moving Truck loads the Box for Shipment, similar to how a Tunnel’s Carrier Protocol encapsulates the Original IP Packet for transport.
- The Moving Truck transports the Boxed Furniture across a series of highways—that is the Internet, stopping occasionally at Gas Stations (that are Routers), for directions.
- Upon arrival, the Moving Truck unloads the Box, similar to how the Tunnel Endpoint strips off the Carrier Protocol, leaving the Original IP Packet now at its intended LAN destination.
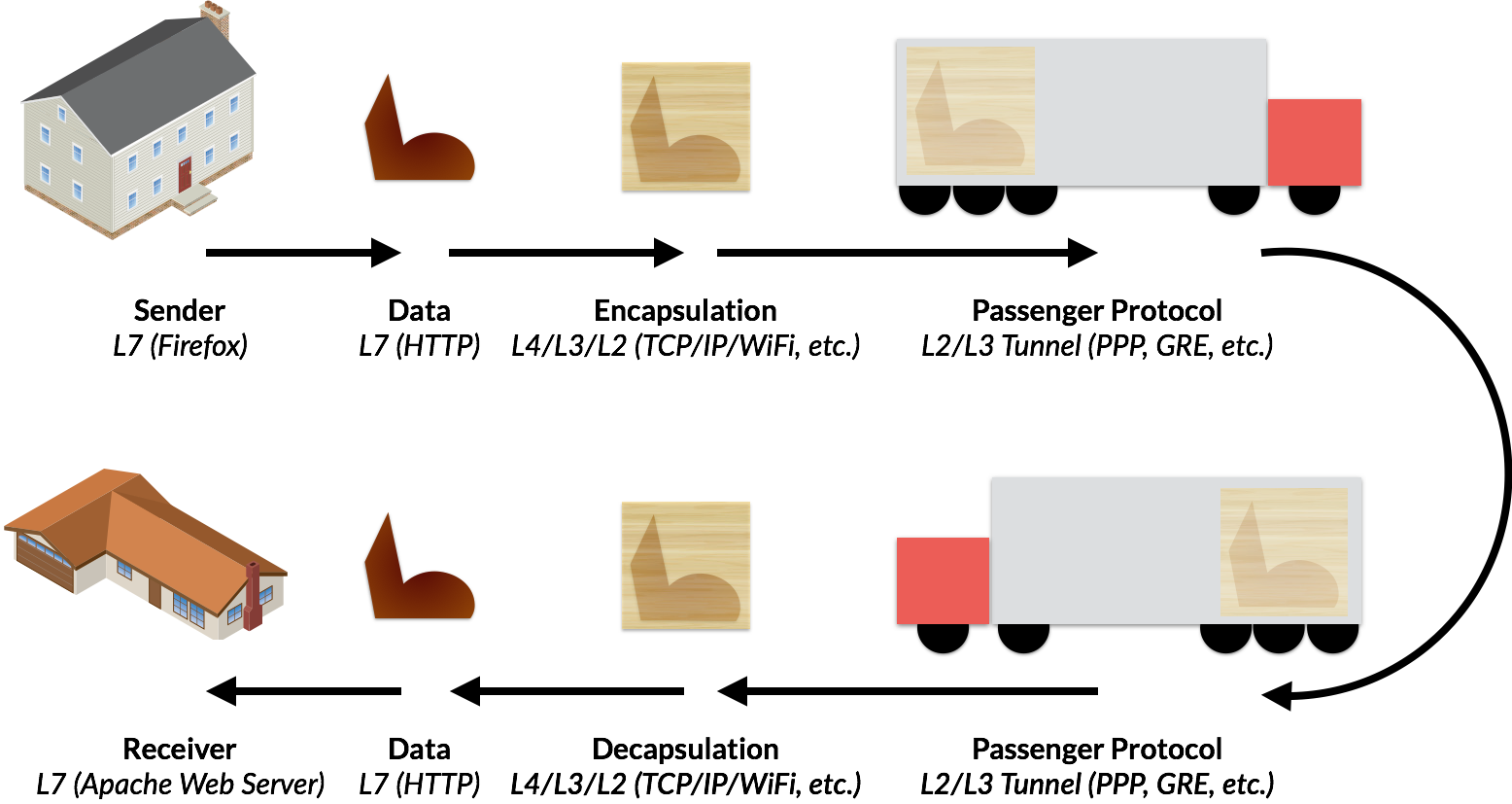
Image 5: Moving Company trucks are analogous to tunneling protocols.